You’re about to launch a new mobile app for your business product. You’ve spent months perfecting its user experience, ensuring seamless functionality, and making it visually stunning. But there’s one question that you haven’t fully answered or are not sure about:
Is your app secure enough to survive a cyberattack?
What if a few months later, after the launch, a hacker exploits a tiny vulnerability in your app’s code? Within hours, millions of user records are leaked, your app is pulled from stores, and legal regulators are knocking at your door. Customers lose trust. Investors panic. Your brand, once a leader, is now a cautionary tale.
What a nightmare! Right? Unfortunately, it’s a reality if you overlook mobile application security. Cybercriminals don’t just go after the big names—they go after any app that handles sensitive data. Whether it’s banking, e-commerce, healthcare, or even an internal enterprise tool, every weak mobile application security is a potential entry point for an attack.
The good news? You don’t have to be the next victim.
The blog isn’t about basic security tips. It’s a comprehensive, high-level security checklist tailored for your business. If you want to protect your business, your customers, and your bottom line, let’s dive into what truly matters in mobile application security.
What is Mobile Application Security?
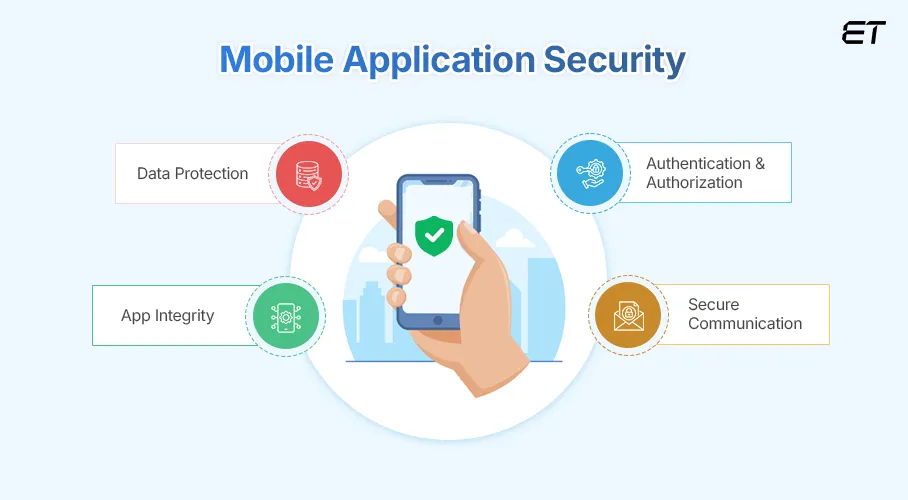
Mobile application security refers to protecting apps from threats and vulnerabilities that could compromise data, steal sensitive information, or harm your users and business. It involves a set of practices, technologies, and protocols designed to keep your mobile apps safe from hackers and cybercriminals. This includes:
- Data Protection: It ensures that sensitive information, such as your user credentials, financial details, or medical records, is securely stored and transmitted without the risk of exposure.
- App Integrity: It prevents attackers from altering or tampering with your app’s code, functionality, or features to exploit it for malicious purposes.
- Authentication and Authorization: It verifies that only authorized users can access the app and its features using mechanisms like usernames, passwords, multi-factor authentication (MFA), etc.
- Secure Communication: It ensures that data exchanged between the app and the server is encrypted and secure, so hackers can’t intercept or alter it during transmission.
Secure your mobile apps with expert protection and safeguard your digital future starting today!
Why Does Mobile Application Security Matter?
The usage of mobile applications has increased immensely, making the stakes higher. Here’s why mobile application security is absolutely essential:
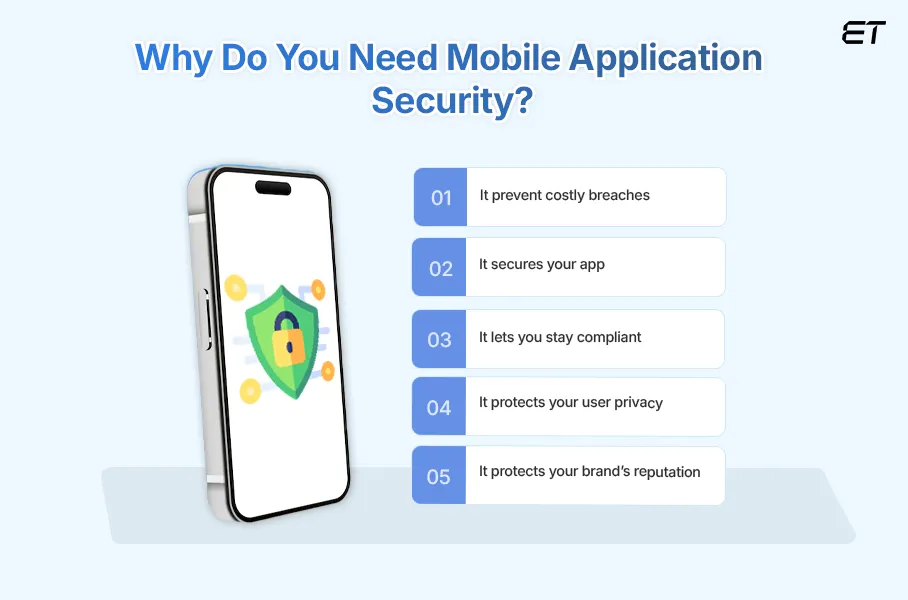
1. Protection Against Data Breaches
One of the primary reasons for implementing strong security for mobile applications is to prevent data breaches. When your apps aren’t secure, hackers can exploit vulnerabilities to steal your sensitive data, such as personal information, financial details, or login credentials. They can then use those stolen data for identity theft, fraud, or sold on the dark web.
For example, a breach of a banking app could result in the theft of millions of users’ banking information, leading to massive financial loss and a shattered reputation.
2. Safeguarding User Privacy
Apps store and process a wealth of personal information, like name, address, phone number, payment methods, and more. Users trust your business to protect this data, and any failure in security can lead to privacy violations.
In many cases, breaches of privacy have legal consequences, as seen in regulations like the General Data Protection Regulation (GDPR), which imposes heavy fines if you mishandle your user’s data. A secure app ensures that users’ private information is only accessible to those with the right authorization.
3. Maintaining Trust and Brand Reputation
Trust is a vital asset for every organization. Customers who download your app expect it to function smoothly and securely. If your app becomes a target of a cyberattack and user data is compromised, it can lead to a loss of trust that is difficult, if not impossible, to rebuild.
A secure mobile application reflects your brand’s commitment to protecting users and their data. On the other hand, a breach can damage your reputation and erode customer confidence, which can lead to lost revenue and a negative brand image.
4. Preventing Financial Loss
Cyberattacks can be costly. Beyond the potential loss of sensitive data, you may incur significant expenses from incident response, legal fees, and compliance-related fines. The financial consequences of not securing an app are severe.
According to IBM’s Cost of a Data Breach Report 2023, the average data breach cost is $4.45 million. A security breach in a mobile application security can expose a company to various liabilities, especially if personal or financial data is involved.
5. Complying with Legal and Regulatory Requirements
Various industries, such as finance, healthcare, and retail, are governed by strict data privacy and security regulations. For example, HIPAA (Health Insurance Portability and Accountability Act) demands that patient information be secured on mobile devices and during transmission.
Similarly, the Payment Card Industry Data Security Standard (PCI-DSS) mandates that payment processing apps meet specific security requirements.
Failing to comply with these regulations can lead you to hefty fines and legal penalties. Implementing robust mobile security testing ensures that your app adheres to these standards and avoids costly legal repercussions.
6. Preventing Fraud and Cyberattacks
Mobile apps are increasingly being targeted for fraud. Attackers use methods like phishing, man-in-the-middle attacks, or even malware to steal user’s data or inject malicious code into the app. Mobile security applications can prevent these types of attacks by using techniques like encryption, certificate pinning, and secure coding practices.
For instance, ensuring that data is transmitted over a secure network connection (SSL/TLS) helps you to protect it from interception during the process.
Fortify your mobile apps with next-gen security and safeguard your digital assets!
Common Mobile Application Security Vulnerabilities
Understanding the most common vulnerabilities in mobile application security is crucial for you to mitigate risks proactively. Let’s glance at the most frequent security flaws that could expose your mobile application security to cyber threats.
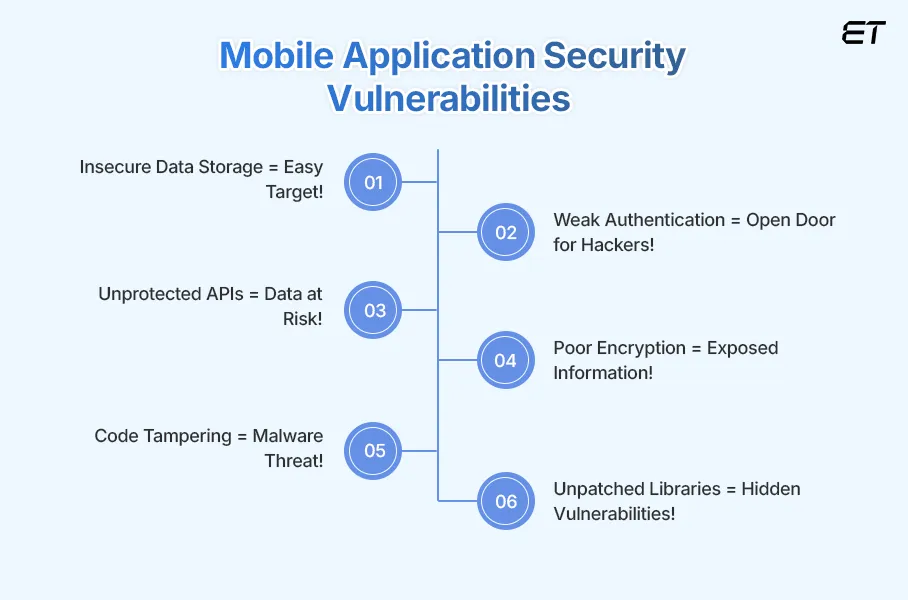
1. Insecure Data Storage
One of your developers’ most significant mistakes is storing sensitive data in an insecure location, making it easily accessible to hackers. If an app saves user credentials, payment information, or personal details without proper encryption, an attacker who gains access to the device can extract this data.
How does this happen?
- Some developers store data in plaintext within app storage, SQLite databases, or SharedPreferences on Android, which can be accessed by other apps or malware.
- Lack of encryption means that if a hacker gains access to the device, they can extract sensitive information directly.
- Jailbroken/rooted devices make it even easier for attackers to access unprotected stored data.
2. Weak Authentication & Poor Authorization Controls
Authentication ensures that only legitimate users can access the app, while authorization defines what users are allowed to do within the system. Weaknesses in either of these areas create an easy entry point for attackers.
How does this happen?
Allowing weak passwords like “123456” or “password” makes it easy for attackers to guess credentials.
No multi-factor authentication (MFA) means attackers can compromise an account with just a stolen password.
Session hijacking occurs when authentication tokens aren’t securely stored, allowing hackers to take over user sessions.
3. Unprotected APIs
APIs (Application Programming Interfaces) allow mobile apps to communicate with servers. However, if they are not properly secured, they can become an open gateway for cyberattacks.
How does this happen?
- APIs exposing too much data (e.g., sending unnecessary user details) can lead to data leaks.
- No authentication or weak API keys allow attackers to make unauthorized API calls.
- Improper rate limiting enables attackers to perform brute-force attacks on API endpoints.
4. Poor Encryption Practices
Encryption is essential for protecting sensitive information as it moves between a user’s device and a server. However, many apps either use outdated encryption methods or fail to encrypt data at all, making it vulnerable to interception.
How does this happen?
- Using outdated encryption protocols like SSL 3.0 instead of the latest TLS versions.
- The lack of certificate pinning allows attackers to intercept traffic using fake security certificates.
- Plaintext data transmission means that hackers can read intercepted messages in human-readable form.
5. Code Tampering & Reverse Engineering
If an attacker modifies your app’s code, they can inject malware, steal your user credentials, or trick them into downloading a fake version of your app.
How does this happen?
- Cybercriminals decompile an app’s APK or IPA file, revealing the source code.
- Hackers inject malicious code to bypass security controls.
- Attackers create clone apps that look identical but steal user data.
6. Insecure Third-Party Libraries & Dependencies
Many mobile application security relies on third-party libraries for features like authentication, analytics, and UI components. However, using outdated or compromised libraries can introduce security risks.
How does this happen?
- Developers fail to update libraries, leaving security vulnerabilities unpatched.
- Attackers inject malware into open-source libraries, which unknowingly are incorporated into apps.
7. Lack of Secure Session Management
Session management ensures that a user remains logged in securely without exposing their data to unauthorized access. Weak session handling can lead to session hijacking attacks, where an attacker steals an active session and gains access to a user’s account.
How does this happen?
- Apps store session tokens in unsecured locations like local storage.
- Tokens never expire, allowing attackers to reuse old tokens indefinitely.
Want to shield your front end from threats? Learn the top security best practices you need!
The Core Security Checklist and Best Practices for Your Mobile Application Security
A well-structured mobile application security checklist ensures that your app is resilient to cyber threats and meets compliance requirements. Below, we’ll walk through a comprehensive security checklist.
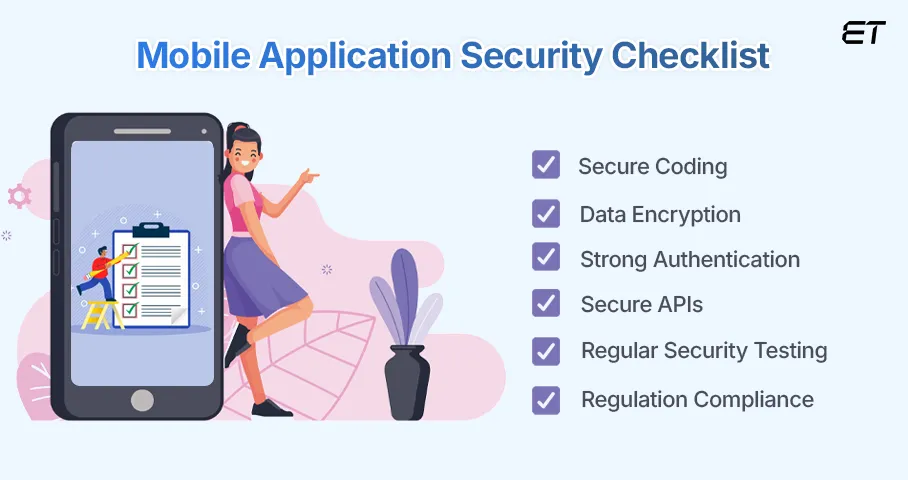
1. Secure Coding Practices
Secure coding is the first line of defense against cyberattacks. Writing clean, well-structured, and security-focused code helps you minimize vulnerabilities and prevent common exploits.
Best Practices of Secure Coding Practices
- Follow Secure Coding Standards: Adhere to guidelines like OWASP Mobile Security Testing Guide (MSTG) to reduce security risks.
- Minimize Code Exposure: Use code obfuscation to make the source code harder to reverse engineer. To minimize code exposure, you can use tools like ProGuard for Android and iOS Obfuscator.
- Prevent SQL Injection & Code Injection: Validate all user inputs to avoid execution of malicious code. You should use parameterized queries instead of raw SQL queries.
- Regularly Update and Patch Code: Fix vulnerabilities as soon as they are discovered. Keep third-party dependencies updated to prevent security gaps.
- Use Secure Cryptographic Libraries: Avoid outdated algorithms like MD5 and SHA-1; instead, use AES-256 and SHA-256 for encryption.
2. Data Security and Encryption
Data security ensures that your confidential user information is protected, even if a hacker gains access to the device or the app.
Best Practices for Data Security and Encryption
- Encrypt Data at Rest and in Transit: You should store sensitive data using AES-256 encryption and transmit it securely using TLS 1.3 to prevent eavesdropping.
- Avoid Storing Sensitive Data Locally: If you’re storing data on mobile, use secure storage solutions like Android Keystore or iOS Keychain.
- Use Tokenization for Sensitive Information: Replace your sensitive data with tokens to protect it from unauthorized access.
- Implement Secure Key Management: Store all your encryption keys in a safe section for secure key management. Do not store them within the app’s codebase where they can be found easily.
3. Strong Authentication and Authorization
To prevent unauthorized data breaches, ensure only authorized users can access certain important parts of the app.
Best Practices for Strong Authentication and Authorization
- Implement Multi-Factor Authentication (MFA): MFA is among the best and most widely used processes. It requires a second authentication factor like OTP, biometrics, or authentication apps to log into your app, enhancing your mobile application security.
- Enforce Strong Password Policies: Ensure that when a user downloads your app, they must set passwords that are at least 12 characters long, with a mix of uppercase, lowercase, numbers, and special characters. This makes the password strong and difficult to hack.
- Use OAuth 2.0 and OpenID Connect: These modern authentication frameworks securely manage your user’s access while reducing the risk of credential theft.
- Limit Login Attempts: Implement account lockout mechanisms after multiple failed login attempts. This will prevent brute-force attacks.
- Role-Based Access Control (RBAC): Restrict access to certain app features based on user roles and permissions.
4. Secure API Communication and Network Protection
APIs act as the bridge between your mobile app and backend services. If you do not secure your APIs properly, they can become an easy entry point for attackers to intrude.
Best Practices for Secure API Communication and Network Protection
- Use API Authentication and Access Controls: Protect APIs with OAuth 2.0, API keys, and JWT tokens to ensure only authorized apps can access them.
- Encrypt Data in Transit with TLS 1.3: Enforce end-to-end encryption for all your API calls to prevent Man-in-the-Middle (MITM) attacks.
- Implement API Rate Limiting: Restrict the number of API calls per user to prevent DDoS (Distributed Denial of Service) attacks.
- Enable Certificate Pinning: This ensures that your app only communicates with trusted servers, blocking fake SSL certificates used by attackers.
- Regularly Audit and Monitor API Traffic: You can use tools like API gateways and firewalls to detect and block malicious requests.
5. Mobile Application Security Testing
Regular mobile application security testing is crucial to identify and fix vulnerabilities before hackers exploit them.
Best Practices of Mobile Application Security Testing
- Perform Static and Dynamic Application Security Testing (SAST & DAST): SAST scans the app’s source code for security weaknesses. DAST tests the app in a real-world runtime environment to identify vulnerabilities, strengthening your mobile application security.
- Conduct Regular Penetration Testing: Ethical hackers usually mimic real-world attacks that help them uncover hidden vulnerabilities in your mobile application security.
- Implement Runtime Application Self-Protection: RASP helps you detect and block attacks in real-time while the app is still running.
- Use Automated Security Scanners: Running security tests every time manually can be daunting. Therefore, you can use tools like Burp Suite, OWASP ZAP, and MobSF that help you automate security testing without any manual intervention.
- Continuously Monitor for Threats: Continuous monitoring is mandatory to avoid any unexpected situation. You can use AI-powered threat intelligence solutions to detect suspicious activity and prevent zero-day attacks.
6. Compliance with Security Standards and Legal Regulations
Ensuring compliance with global security regulations is mandatory to avoid legal penalties and protect your user privacy.
Best Practices for Compliance with Security Standards and Legal Regulations
- Follow Industry-Specific Compliance Standards: Compliances like the following are mandatory to follow:
– GDPR (for personal data protection in the EU)
– HIPAA (for healthcare applications handling patient data)
– PCI-DSS (for mobile payment security)
– ISO 27001 (for general information security best practices)
- Create a Transparent Privacy Policy: Inform your users clearly about the data collection, storage, and sharing practices you follow. This will create trust and loyalty among your customers for your app.
- Enable Secure User Consent Mechanisms: Ask your users for consent before collecting or storing any of their information. Implement opt-in permissions and allow your users to manage their privacy settings.
7. Secure Session Management and Logout Mechanisms
Session management ensures that your users can stay securely logged in without leaving their accounts vulnerable to hijacking.
Best Practices for Session Management and Logout Mechanisms
- Use Secure Session Tokens: Store session data using JWT or OAuth tokens instead of cookies.
- Set Session Expiry and Auto-Logout: Automatically log out users after a period of inactivity. This way, even if they forget to log out manually, they’ll be assured that their account is safe.
- Invalidate Tokens After Logout: Ensure that session tokens expire immediately when the user logs out.
- Enable Biometric Authentication for Reauthentication: Allow users to re-enter apps securely with fingerprint or facial recognition.
8. Continuous Security Monitoring and Incident Response
Even with strong security measures, constant monitoring is mandatory to detect and respond to new threats that may arise.
Best Practices for Security Monitoring and Incident Response
- Implement Real-Time Security Logging: Monitor app activity for suspicious behavior and unauthorized access.
- Set Up Intrusion Detection Systems (IDS): This enables you to detect security breaches and block malicious activities.
- Have an Incident Response Plan in Place: Define clear steps for handling data breaches, malware infections, and other security incidents. This way, your developers are aware of the steps they need to follow, even without anyone watching over them.
- Perform Regular Security Audits: You need to conduct quarterly or bi-annual security reviews to ensure continuous protection of your mobile application security.
Wrapping Up!
Mobile application security isn’t just about compliance—it’s about protecting your users, business reputation, and financial assets. Implementing the above core security practices will help prevent cyberattacks and ensure your app remains safe and trusted.
Implementing this checklist lets you stay one step ahead of cyber threats. Remember that cybersecurity is not a one-time effort; it’s a continuous process of testing, improving, and adapting to new threats.
As cyberattacks grow more sophisticated, the question isn’t if your mobile app will be targeted but when. The time to act is now because securing your mobile application security today means protecting your business, customers, and future.
Secure your mobile apps with cutting-edge protection now! Click below to connect with our experts.
Frequently Asked Questions
1. What is mobile application security, and why is it important?
Mobile application security is the practice of protecting your apps from threats like data breaches, unauthorized access, and malicious attacks. It is crucial to safeguard sensitive data, protect user privacy, and ensure regulation compliance. Weak security can lead to financial loss, legal penalties, and reputational damage.
2. How can I secure my mobile app from cyber threats?
To secure your app from cyber threats:
- Implement strong encryption
- Use multi-factor authentication
- Regularly update third-party libraries
- Perform security testing like penetration testing
Always secure your APIs and keep user data safe with secure storage solutions.
3. What are the most common mobile app vulnerabilities?
Common mobile app security vulnerabilities include:
- Insecure data storage
- Weak authentication
- Unprotected APIs
- Poor encryption practices
- Code tampering
These flaws can expose your sensitive user data, making apps susceptible to attacks and breaches.
4. How can I ensure my mobile app complies with security regulations?
To ensure your mobile app security compliance, follow security standards like GDPR, HIPAA, and PCI-DSS. Implement data encryption, conduct regular security audits, and use secure coding practices. Always stay updated with regulations to avoid legal penalties and protect user data.

An accomplished professional with 9 years of experience in mobile application development, Abhilash holds an MCA and specializes in creating seamless Android (Kotlin, Java) and iOS applications. Proficient in Flutter framework using Dart, Firebase, Dependency Injections, Dagger, and Jetpack Compose, he stays at the forefront of technology by exploring trends like iOS Swift-UI. Abhilash’s innovative approach and technical expertise ensure exceptional user experiences and efficient solutions.