Before we get started, let me tell you that this blog is going to be purely for techies who are looking forward to a comprehensive information about XSS. Cross Site Scripting, shortly known as (XSS), is a type of attack done by bypassing the script access by an attacker. It is commonly carried out from user’s IP address; some website logs might not have evidence of CSRF. Exploits are under-reported, at least publicly, the common example is:
Ex. The online banking web application
OCCURANCES:
To execute infected javascript code into user’s web application, the attacker can use some techniques. They can even insert the string into web application as an infected script.
Please see below code which will explain you more:
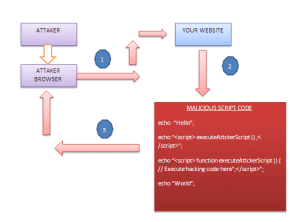
echo “Hello”;
echo “<script> executeAttckerScript();</script>”;
echo “<script> function executeAttckerScript (){ // Execute hacking code here”;</script>”;
echo “World”;
The most easily accessible platform for attacker is Javascript.
It will be helpful for you to identify XSS:
- Strong knowledge of Javascript, HTML
- Basic knowledge of HTTP client-server communication
- Identify the malicious website
If you are going to test your own site, you have to check every page in your site for the vulnerability.
- Testing the Vulnerability:
Initially, you have to find the input boxes so that you can inject own script, like; search box, username, email, password etc.
There are maximum changes of inserting scripts from input fields on your website.
XSS ATTACK SKELETON:
- Attacker attacks your website with malicious code.
- This code is executed on your website end.
- After execution, it will be redirected to attacker end with required data.
PREVENTION:
There are simple rules that need to follow everywhere: Encode every data that is given by a user. If data is not provided by a user but given by the GET parameters, encode these data too. Even a POST form can contain XSS.
Following are the basic guidelines that need to be sanitized before used in your website.
- URL
- HTTP Referrer Objects
- GET parameter
- POST parameter
- Location
- Referrer
- Location
- URL
- cookie data
- headers data
- data validation
- encode all <, >, ‘ and “.
Some examples of encoding are:
- & –> &
- < –> <
- > –> >
- ” –> "
- ‘ –> ‘
- / –> /
htmlspecialchars() function will play this role in PHP.
It encodes all HTML tags and special characters.
Ex. $string = htmlspecialchars($string);
A regular expression rule is also important to avoid XSS as:
$string= preg_replace(‘/(&#*w+)[x00-x20]+;/u’, ‘$1;’, $string);
$output = preg_replace(‘/(&#x*[0-9A-F]+);*/iu’, ‘$1;’, $output);
As a web developer, it is our responsibility to create a secure web application to make user data more secured.