
SaaS Security Guide 2025: Best Practices, Tools and More
- SaaS security protects sensitive data stored and processed in cloud applications.
- Challenges like Shadow IT, weak access controls, and unauthorized sharing pose business risks.
- Multi-Factor Authentication (MFA) and SSO strengthen identity protection.
- Role-Based Access Control (RBAC) prevents over-privileged accounts.
- Encrypting data at rest and in transit safeguards against breaches.
- Training employees reduces human errors and shadow AI risks.
- Tools like CASB, SSPM, IAM, and SIEM enable proactive SaaS protection.
28% of SaaS companies faced a data breach in the past year. One-third of them experienced an attack more than once, indicating most companies aren’t ready for these cases.
If you’re a CTO or Cybersecurity Head, it’s high time you took SaaS security seriously.
Unlike traditional on-prem systems, SaaS shifts control outside your data center. Sensitive information now resides on third-party platforms, accessible from anywhere, on any device. This flexibility fuels growth, but also opens the door to compliance headaches and insider threats.
So, the stakes are higher than ever. A single overlooked software vulnerability can lead to data breaches, regulatory fines, and broken customer trust.
To help you navigate such cyber risks efficiently, this guide discusses what is SaaS security and best practices to ensure it. We’ll also talk about the top SaaS security tools.
Partner with us to build custom SaaS solutions.
What is SaaS Security?
SaaS security is the practice of protecting data, users, and applications within cloud-based software environments.
Unlike traditional on-premise systems, SaaS platforms operate outside your organization’s perimeter, which means less visibility and control over infrastructure. So, security must focus on identity management, data encryption, continuous monitoring, and vendor risk assessment.
At its core, security SaaS strategies ensure the following:
- Improved Data Protection – Safeguards sensitive information from leaks, breaches, and unauthorized exposure across SaaS environments and connected apps.
- Better Identity and Access Control – Ensures only authorized users gain access, with strict rules on permissions, authentication, and activity management.
- Efficient Compliance Assurance – Helps align with regulatory frameworks like GDPR, HIPAA, and SOC 2, reducing risks of penalties or reputational damage.
- Real-time Security Checks – Provides real-time visibility into configurations, login patterns, and unusual behaviors, enabling rapid detection and response.
The goal is to secure sensitive information while enabling employees to use SaaS tools productively.
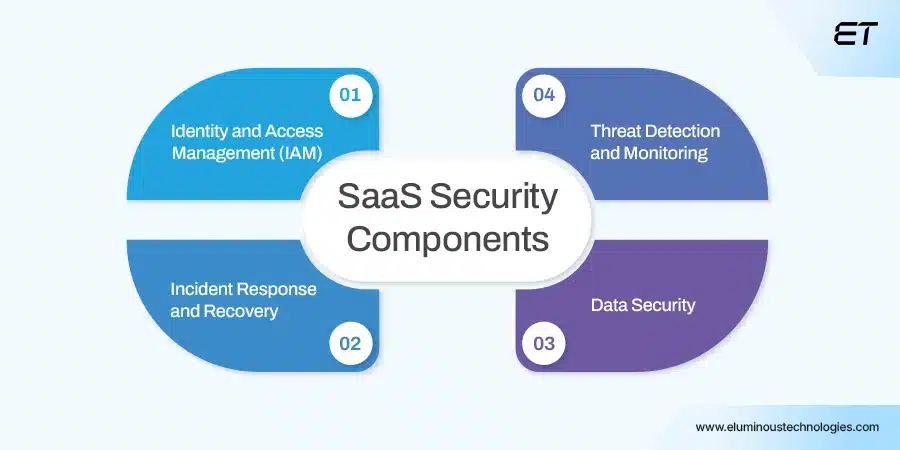
Key Components of SaaS Security
SaaS security is built on multiple layers, each addressing a specific risk area. Together, they create a resilient framework for protecting cloud-based applications.
The core components include:
- Identity and Access Management (IAM) – Controls who can access SaaS apps and enforces policies like MFA, SSO, and RBAC.
- Data Security – Ensures encryption, secure backups/recovery, and safeguards against accidental sharing or sensitive data leaks.
- Threat Detection and Monitoring – Continuously scans activity logs, configurations, and user behavior to spot anomalies or potential breaches.
- Incident Response and Recovery – Provides playbooks and processes to quickly contain, investigate, and recover from security incidents.
These security SaaS pillars allow business leaders to protect their apps without slowing innovation.
Common SaaS Security Challenges Putting Your Business at Risk

Almost 55% of employees adopt SaaS platforms without proper security oversight. This indicates how tightening security protocols is falling behind with increasing SaaS adoption.
Plus, SaaS apps offer a convenient solution to customers. So, tightening security protocols and addressing risks is more important than ever. Here are the crucial SaaS security issues you need to address right now to safeguard your business.
| Challenge | Why It’s a Risk | Solution |
| Shadow IT | Employees adopt unsanctioned apps, creating blind spots for security teams. | Use CASBs/SSPM tools to discover and monitor all SaaS usage. |
| Misconfigured SaaS Applications | Incorrect settings expose data to unauthorized users or the public. | Regular configuration audits and automated posture management tools. |
| Weak Access Controls | Stolen or weak credentials enable unauthorized access to sensitive data. | Enforce MFA, SSO, and role-based access policies. |
| Data Leakage and Unauthorized Sharing | Sharing sensitive data externally increases breach and compliance risks. | Apply DLP policies and monitor file-sharing permissions. |
| Regulatory Gaps | Non-compliance with GDPR, HIPAA, or SOC 2 results in heavy fines. | Align SaaS usage with frameworks and run compliance checks. |
Continuous security monitoring and assessments are key to implementing these strategies successfully.
SaaS Security Best Practices: 6 Ways to Shield Your Business Operations
Preparing SaaS security strategies is now a core part of any enterprise plan. The right approach safeguards internal data, protects customer trust, and future-proofs your enterprise against evolving threats.
Let’s explore some actionable steps for building a more resilient SaaS environment.
1. Implement Multi-Factor Authentication (MFA) and Single Sign-On (SSO)
Multi-Factor Authentication (MFA) enhances security by requiring multiple verification factors, such as passwords, biometrics, or tokens, before granting system access.
Single Sign-On (SSO) allows users to securely log in once and access apps without repeatedly entering passwords. Together, these practices ensure only the right people gain access.
Business leaders can implement the safeguards through these steps:
- Enable MFA Across All Platforms – Request an additional factor, such as OTP, biometric, or hardware token, beyond passwords.
- Adopt a Centralized SSO Solution – Set up access through one secure login, reducing password fatigue and IT overhead.
- Mandate MFA for Privileged Accounts – Protect administrators and executives who have the highest access risks.
- Continuously Monitor Login Activity – Flag unusual attempts, location-based anomalies, or repeated failures.
For example, a global retail firm can roll out SSO integrated with MFA for employees. They can log in once to securely access 50+ SaaS tools, reducing password resets and strengthening access control.
2. Detect and Govern Shadow AI Issues

Approximately 55% of employees utilize Gen AI tools, with 84% of them exposing their organizational data publicly. This shows the shortcomings in AI governance among companies.
This has given rise to Shadow AI, which refers to unapproved AI tool usage, creating security and governance risks. Business leaders can counter this with structured actions:
- Identify Hidden Usage – Deploy SaaS Security Posture Management (SSPM) or CASB tools to detect unapproved AI apps.
- Create an AI Governance Policy – Define which apps are allowed, restricted, or prohibited, and clearly communicate this to your teams.
- Enable Centralized Access Controls – Integrate sanctioned AI apps with SSO and enforce MFA to prevent risky logins.
- Limit Data Exposure – Utilize data loss prevention (DLP) tools to control the flow of sensitive information into AI apps.
Additionally, detect and close abandoned employee software accounts when they part ways with the firm. This prevents cybercriminals from exploiting these accounts and accessing secure data.
Curious to know more about AI security risks?
3. Enforce Role-Based Access Control (RBAC) with Strong IAM Policies
RBAC ensures users only have the required access, minimizing risks of misuse or accidental data exposure. For business leaders, the goal is to align permissions with responsibilities while reducing the attack surface.
Actionable steps include:
- Define User Roles Clearly – Map roles to business functions (e.g., finance, HR, IT) with specific access needs.
- Assign Least-privilege Access – Give employees only the minimum rights required for their job functions.
- Regularly Review Permissions – Conduct quarterly audits to revoke outdated or unnecessary access.
- Automate Provisioning and Deprovisioning – Use IAM (Identity and Access Management) tools to ensure timely updates when employees change roles or exit.
Moreover, grant just-in-time access, offering permissions only when needed, reducing standing privileges that attackers could exploit.
4. Encrypt Data at Rest and in Transit
Data encryption ensures sensitive information remains protected, whether it’s stored in databases (at rest) or moving between systems (in transit). This helps safeguard customer trust and compliance while reducing breach impact.
Here’s how to implement the strategy:
- Mandate Encryption by Default – Require all SaaS vendors to use AES-256 or equivalent encryption for stored data.
- Secure Data in Transit – Enforce TLS/SSL protocols for all communication between users, applications, and APIs.
- Protect Encryption Keys – Use Hardware Security Modules (HSMs) or managed key services to avoid unauthorized access.
- Enable Field-level Encryption – Apply encryption selectively to highly sensitive fields like SSNs, financial data, or health records.
You can also set up automated alerts to detect unencrypted data flows or weak protocols before they become vulnerabilities.
5. Train Employees on SaaS Security

Training employees about the SaaS security best practices is as important as implementing the security strategies mentioned above. Spread awareness and knowledge via these steps:
- Run Regular Training Sessions – Conduct quarterly workshops on phishing, password hygiene, and safe SaaS usage.
- Simulate Real Attacks – Use phishing simulations to test awareness and highlight vulnerabilities in employee behavior.
- Share Policy Updates Clearly – Communicate which SaaS tools are approved and which are restricted to prevent shadow IT.
- Measure Progress – Track training participation, test results, and improvements over time to understand effectiveness.
Pro Tip: Offer quizzes, rewards, or leaderboards to keep security training engaging. Make this training mandatory for professionals across all departments for overall protection.
Searching for trained experts to power your software success?
6. Vet Third-Party SaaS Plugins Carefully
Third-party plugins can extend SaaS functionality, but they also widen the attack surface. Unvetted or outdated plugins create hidden risks. Regularly review support, updates, and version history to ensure integrations remain secure and reliable.
Follow these processes to tackle plug-ins and improve SaaS security:
- Check Vendor Credibility – Choose plugins from reputable providers with a clear track record of security and ongoing support.
- Review Update History – Avoid plugins that haven’t released updates in years, as outdated code is a red flag.
- Monitor Plugin Performance – Regularly audit usage and revoke plugins no longer supported or needed.
- Align with IT Policies – Ensure all plugin approvals undergo a security review to prevent shadow integrations.
Further, it’s essential to test new plugins for vulnerabilities before deployment.
Must-Have SaaS Security Tools for Every Business Leader
After learning what is SaaS security and its best practices, let’s explore SaaS security tools. These software solutions address various security aspects, including cloud protection and posture management, helping businesses stay compliant.
The table delves into some essential tool categories.
| Tool Category | Purpose | Examples |
| IAM & PAM (Identity & Privileged Access Management) | Controls user identities, enforces MFA/SSO, and secures privileged accounts from misuse or credential theft. | CyberArk |
| Zero Trust Security Tools | Enforces “never trust, always verify” policies, validating every user, device, and session before granting access. | Palo Alto Prisma |
| CASB (Cloud Access Security Brokers) | Provides visibility into SaaS usage, prevents shadow IT, and enforces data policies across cloud apps. | Netskope |
| SSPM (SaaS Security Posture Management) | Continuously monitors and fixes misconfigurations, ensuring SaaS apps meet compliance and security standards. | Obsidian |
| SIEM (Security Information and Event Management) | Collects and analyzes logs to detect suspicious activity for real-time threat response. | Microsoft Sentinel |
When combined, these tools give leaders end-to-end SaaS visibility, proactive risk management, and faster incident response.
Learn why Posture Management is critical for your business.
The Bottom Line
SaaS security is a frontline business priority, as these apps power everything from customer engagement to internal collaboration. One weak link can jeopardize data, compliance, and trust.
That’s why leaders are combining best practices like MFA and RBAC with powerful tools such as IAM, Zero Trust, CASB, and SSPM. This way, building a layered defense that adapts to evolving threats is achievable.
Ultimately, the organizations prioritizing SaaS security gain a competitive edge: they move faster, stay compliant, and win customer trust.
Your secure SaaS journey starts now.
Frequently Asked Questions
1. What is SaaS security?
SaaS security is the practice of protecting data, users, and applications in cloud-based SaaS software by applying controls, policies, and tools. It prevents breaches, unauthorized access, and compliance risks.
2. What are the 5 key security elements of the SaaS model?
The five key security elements include data protection, identity management, access control, threat detection, and regulatory compliance, ensuring safe cloud app usage.
3. Is CyberArk a SaaS?
Yes, CyberArk offers SaaS-based solutions for identity security and privileged access management. It also provides on-premises deployment options.



