Do you know that in 2023, the average cost of a data breach worldwide was $4.45 million , a 15% rise in only three years?
According to T-Mobile, in 2023, around 836 customers’ personal information was stolen in the company’s second data breach of the year, whereas over 37 million subscribers were impacted by the company’s first data incident.
A web application penetration methodology is the talk of the town to find and fix the most critical security vulnerabilities, misconfigurations, and business logic flaws affecting your company.
Through this guide, we will understand web application penetration testing and its different methodologies. You’ll also learn the steps to perform security testing on a web application and the popular tools used during a web application penetration testing methodology.
What’s your call on the below stats?
Data Breach Stats for 2023
| Number of incidents | 1404 |
| Number of breached records | 5,951,612,884 |
| Biggest data breach of 2023 | DarkBeam (3.8 billion breached records) |
The digital era creates new targets for cyberattacks in addition to new opportunities. Ensuring the safety of systems and applications is critical for all businesses today.
- How can you be sure that your business’s information is secure?
- How can you compare hackers’ advanced techniques with your cybersecurity infrastructure?
Don’t worry; all such issues are addressed by penetration testing!
A pentest provider’s prescribed approach for carrying out a pentest on a target network or website is known as their penetration testing methodology. Various penetration testing approaches can be employed based on the target business’s category, the pentest’s objective, and its scope.
Regarding web application penetration testing methodologies, there isn’t a one-size-fits-all. Every target enterprise has specific needs when it comes to compliance, security, and tolerance.
This guide on web application penetration testing methodology offers an outline and procedures to assist you in navigating this intricate process. Keep reading to learn about the different stages, their criteria, and the areas that need penetration testing.
First, let’s cover the basics!
What is Web Application Penetration Testing?
Web application penetration testing is a proactive security assessment methodology focused on identifying and mitigating vulnerabilities within web applications.
In order to find vulnerabilities entails trying to breach any number of networks, systems, or applications (such as frontend/backend servers, protocol interfaces, APIs, and applications). For example, unsanitized inputs that could be attacked via code injection.
Skilled ethical hackers, often referred to as penetration testers, employ various tools and techniques to evaluate the security posture of web applications. This process helps organizations identify and address vulnerabilities, protect sensitive data, and ensure the robustness of their web-based systems against potential cyber threats and unauthorized access.
Types of Web App Penetration Testing
Web penetration testing comprises various types, each targeting specific aspects of web applications to identify and address potential vulnerabilities. Organizations can comprehensively assess their web application’s security posture and proactively address potential vulnerabilities by employing a combination of these testing types.
| Type of Pentest | Explanation |
| Black Box Testing | Mimics an external hacker without prior knowledge of the system, helping assess how well the application can withstand real-world attacks. |
| White Box Testing | This involves complete knowledge of the application’s internal structure and source code, allowing for a thorough examination of potential vulnerabilities from an insider’s perspective. |
| Gray Box Testing | Strikes a balance between black and white box testing, providing partial knowledge of the system to simulate an attack by a partially informed attacker. |
| Security Misconfiguration Testing | Evaluate the application for misconfigurations that may expose sensitive data or provide unauthorized access. |
| Session Management Testing | Ensures secure session handling, preventing unauthorized access to user accounts by exploiting flaws in session management. |
| SQL Injection Testing | Focuses on exploiting SQL vulnerabilities to gain unauthorized access to databases and extract or manipulate sensitive information. |
| File Upload Testing | Verifies the security of file upload functionality, preventing malicious uploads that could lead to code execution or unauthorized access. |
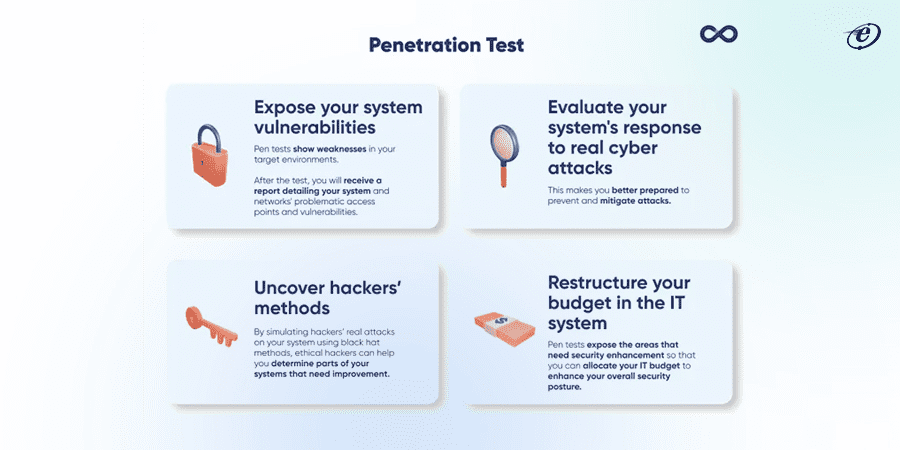
Why is Web Application Penetration Testing Methodology Essential?
A crucial component of any robust security program is penetration testing, which is typically done by a dedicated team of experts. A few key benefits of performing a web application penetration testing methodology are:
-
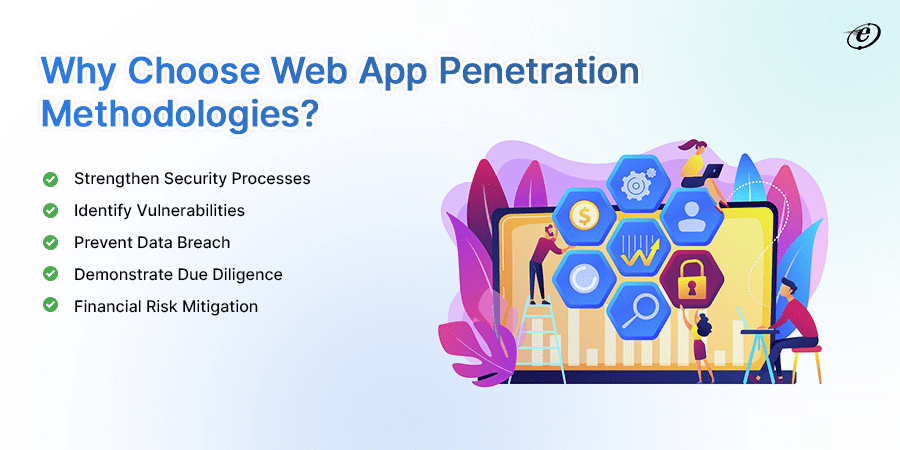
Strengthen Security Processes
Penetration testing strengthens security processes by systematically identifying and addressing system, application, and network vulnerabilities. Through simulated cyberattacks, organizations can proactively mitigate risks, fortify defenses, and ensure a resilient security posture, thereby minimizing the likelihood of successful real-world breaches.
-
Identify Vulnerabilities
Penetration tests reveal cybersecurity plan flaws that may have been previously missed. Pinpoints vulnerabilities in web applications, allowing for proactive mitigation before exploitation by malicious factors, thereby reducing the risk of security breaches.
-
Prevent Data Breach
It helps ensure the confidentiality of sensitive data by identifying and addressing potential loopholes in data handling processes within web applications.
-
Demonstrate Due Diligence
It helps organizations demonstrate their commitment to security, which is crucial in maintaining user trust, preventing reputational damage, and avoiding legal repercussions.
-
Financial Risk Mitigation
Proactively addressing vulnerabilities through penetration testing helps organizations avoid financial losses due to data breaches, legal consequences, and reputational damage.
Must Know Web Application Penetration Testing Methodology
Testing can be done using a variety of well-known and established techniques and standards, but as every web application requires a particular set of tests to be run, testers can also design their own methodology using industry standards as a guide.
We’ll discover some of the most widely used web application penetration testing methodologies in this article, highlighting their main features.
OWASP: Open Web Application Security Project
OWASP is widely recognized for its commitment to improving software security. The OWASP Testing Guide provides a framework for testing the security of web applications. It covers various aspects, including authentication, session management, access controls, and data validation. Its guide is regularly updated to address emerging threats and technologies in the web application landscape.
This web application penetration testing methodology is the most widely employed in the industry (Open Web Application Security Project). The OWASP community is knowledgeable about the most recent technological advancements and the state of security threats. It provides a comprehensive set of instructions for testing online, mobile, and APIs in the modern day. In addition to applications, it comprises people, technologies, and procedures.
Find top 10 API integration tools for developers in 2024.
OWASP provides a variety of guides and resources to help organizations and dedicated developers enhance the security of their web applications. Here are some resources from OWASP:
| Resources | Explanation |
| OWASP Top Ten | It provides information about common vulnerabilities, attack techniques, and mitigation strategies. |
| OWASP Application Security Verification Standard (ASVS) | It consists of security requirements that define the security controls required while designing, developing, and testing modern web applications and services. |
| OWASP Testing Guide | It includes testing techniques, methodologies, and best practices for various aspects of application security, including authentication, authorization, session management, input validation, and more.
|
| OWASP Cheat Sheet Series | It covers various topics, including secure coding practices, authentication, cryptography, and security headers. Each cheat sheet provides practical advice and examples. |
| OWASP SAMM (Software Assurance Maturity Model) | It provides an effective and measurable way for all types of enterprises to analyze and improve their software security posture. |
OSSTMM: Open Source Security Testing Methodology Manual
Another comprehensive framework is the Open-Source Security Testing Methodology Manual (OSSTMM). It includes an overview of web security testing, guidance on interpreting test results, and a focus on what to test rather than how to test it.
The Open-Source Security Testing Methodology, or OSSTMM, was created by ISECOM (Institute for Security and Open Methodologies) and provides a systematic approach to pen testing.
The OSSTMM is a comprehensive and holistic web application penetration testing methodology focusing on operational and security aspects. It covers information security, data networks, wireless networks, and web applications.
OSSTMM emphasizes the importance of understanding the business context and operational environment before diving into the technical assessment. The methodology includes well-defined steps for information gathering, threat profiling, vulnerability research, and exploitation.
The following are the key sections of OSSTMM:
- Information Security: Focuses on safeguarding sensitive data.
- Data Networks: Evaluate security in network infrastructures.
- Wireless Networks: Assesses security vulnerabilities in wireless setups.
- Web Applications: Tests the security of web-based software.
- Operational Environment: Emphasizes understanding the business context.
- Threat Profiling: Identifies potential threats and risks.
- Vulnerability Research: Systematically explores security weaknesses.
- Exploitation: Simulates real-world attacks to test defenses.
- Pre-Engagement: Involves planning and defining the scope of testing.
- Reporting: Provides comprehensive documentation of findings and recommendations.
-
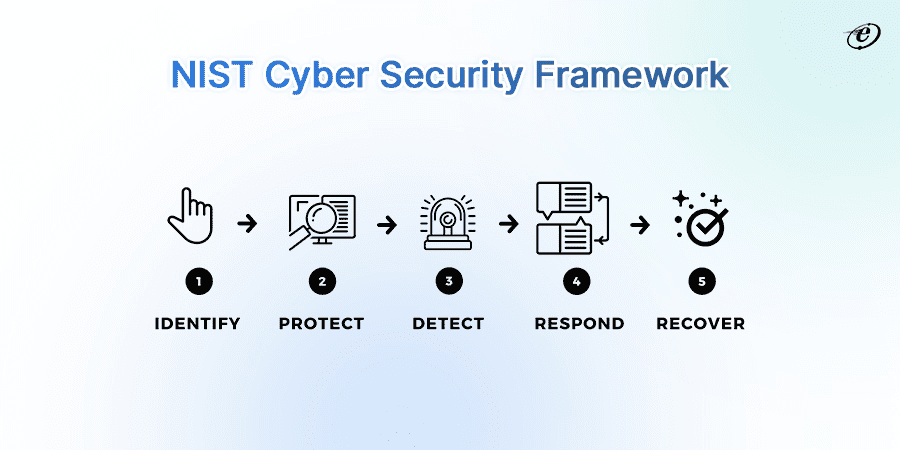
NIST Special Publication 800-115
A federal organization called the National Institute of Standards and Technology advances standards across many industries, including computer security. The NIST Special Publication 800-115 includes technical instructions for doing penetration testing and vulnerability analysis.
This web application penetration methodology is appropriate for companies in the public and private sectors and is in line with the Risk Management Framework (RMF).
NIST 800-115 is solely concerned with the technical components of carrying out a vulnerability assessment and penetration test, whereas OSSTMM offers a wide operational perspective.
Its pen-testing methodology handbook provides an exact and detailed set of instructions to improve the organization’s overall cybersecurity posture. The most recent edition of this security handbook lowers the danger of cyberattacks while highlighting cybersecurity for critical infrastructure.
Key features include:
- Risk Management Integration: Aligns with the Risk Management Framework (RMF), providing a structured approach to security assessments.
- Planning and Execution Guidance: Offers detailed guidance on planning, executing, and documenting security assessments, promoting a standardized and repeatable process.
- Vulnerability Analysis: Provides methodologies for identifying and analyzing vulnerabilities in information systems.
- Threat Emulation: Supports the emulation of real-world threats, allowing organizations to assess their security posture against evolving cyber threats.
- Security Controls Assessment: Facilitates the evaluation of security controls, ensuring that they effectively mitigate risks.
- Applicability to Various Environments: Adaptable for government and private sector organizations, making it a versatile resource for diverse industries.
- Continuous Improvement: Encourages organizations to incorporate lessons learned into future security practices, fostering a culture of continuous improvement.
- Interagency Collaboration: Reflects a collaborative effort involving various agencies, enhancing the comprehensiveness and applicability of the guidance provided.
-
PTES: Penetration Testing Execution Standard
PTES is a comprehensive and well-structured web application penetration testing methodology that outlines the entire penetration testing process. It defines a set of guidelines covering the pre-engagement, intelligence gathering, threat modeling, vulnerability analysis, exploitation, post-exploitation, and reporting phases. PTES focuses on maintaining a consistent and repeatable testing process, promoting professionalism in penetration testing engagements.
The main benefit of this methodology is its technical guide, which contains detailed technical information commands and tools for every stage of penetration testing. The leading web application development companies highly recommend using this framework in case when you need full information about what to test and how to test it.
Key features of PTES include:
- Holistic Approach: PTES covers the entire penetration testing process, including pre-engagement, intelligence gathering, vulnerability analysis, exploitation, post-exploitation, and reporting.
- Threat Modeling: Incorporates threat modeling to identify and prioritize potential threats and risks.
- Exploitation: Simulates real-world attacks to validate vulnerabilities and assess the effectiveness of security controls.
- Reporting Standards: Provides guidelines for clear and comprehensive reporting, ensuring that findings are communicated effectively to stakeholders.
- Adaptability: Adaptable to different environments, technologies, and industries, making it applicable for a wide range of penetration testing engagements.
-
ISSAF: Information Systems Security Assessment Framework
ISSAF, abbreviated as the Information Systems Security Assessment Framework (ISSAF), was created to help web developers evaluate the security of information systems. ISSAF, which security specialists created, offers a comprehensive approach to security assessments by addressing a wide range of security areas.
Technical and management components are divided into two categories. The technical section provides a set of the most crucial guidelines and practices for developing a suitable security assessment process. There are broad suggestions for establishing a successful testing procedure on the managerial side.
This web application penetration testing methodology provides a comprehensive picture of an organization’s security posture by integrating important security domains, facilitating informed decision-making and risk management.
According to experienced web developers, this framework is always up to date-and applicable in the rapidly changing field of information security due to its community-driven methodology.
Key features of ISSAF are:
- Risk Management: Prioritizes security efforts based on risk assessment.
- Application Security: Focuses on secure coding practices and application vulnerabilities.
- Access Controls: Assesses user authentication, authorization, and auditing mechanisms.
- Physical Security: Examines measures for protecting physical access to information systems.
- Incident Response: Guides the development and testing of incident response plans.
- Security Testing: Includes penetration testing, vulnerability assessment, and security audits.
- Documentation and Reporting: Emphasizes clear and thorough reporting for effective communication of assessment findings.
How to do Penetration Testing for Web Applications?
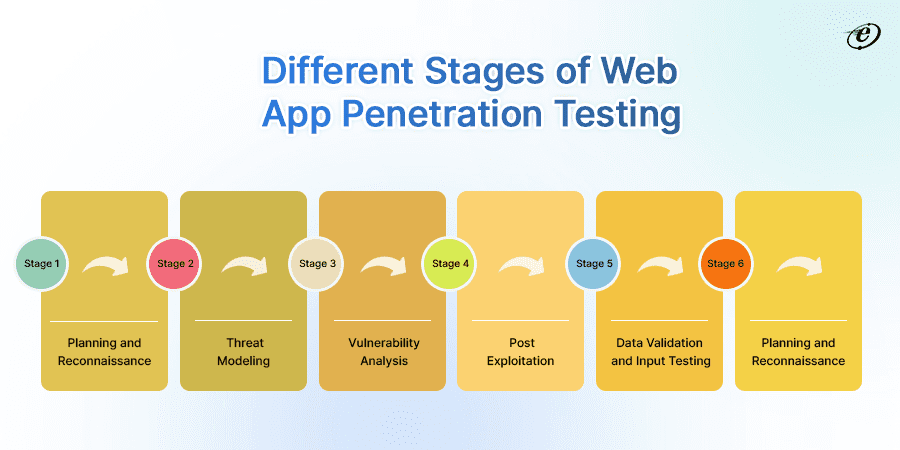
Web application penetration testing involves a systematic approach to identify and remove security vulnerabilities in custom web applications. The methodology typically consists of several stages, each serving a specific purpose. Here are the key stages of a web application penetration testing methodology:
-
Planning and Reconnaissance
The planning stage is the first in the web application penetration testing methodology. A well-crafted plan clears the path through an organization’s convoluted IT infrastructure.
Gathering intelligence on the systems and doing appropriate reconnaissance are essential for a successful penetration test. Custom web application development companies obtain information (such as mail servers, networks, and domain names) to learn more about a target’s operation and any weaknesses. Tools like Recon-Ng, Nmap, Spiderfoot, Metasploit, and Wireshark are frequently used for this.
-
Threat Modeling
Dedicated testers find potential threats in this step and rank them according to likelihood and impact. It entails looking into the application architecture, comprehending data flow, and identifying possible attack points.
Manual discovery and application crawling should be part of this evaluation process to ascertain business functioning from an authenticated and unauthenticated standpoint. An application proxy will also be used to assess packet-level traffic and response headers.
-
Vulnerability Analysis
Testing personnel will use the possible vulnerabilities discovered to gain more access to the system. To record the complete process for future evaluation, every step, tool utilized, location, and entry method for a specific issue is accurately documented. These security vulnerabilities are ranked according to how easily they can be exploited and how much harm they can inflict as part of the penetration testing process. The organization can then order the fixes according to priority.
-
Post Exploitation
In this stage of web app penetration testing, all potential vulnerabilities found in the earlier phases will be taken and used to exploit them as an attacker would.
In penetration testing, post-exploitation is a critical phase where the tester assesses the impact of successful exploitation. It involves exploring compromised systems, pivoting to additional targets, and maintaining access. The objective is to understand the extent of the compromise and identify potential risks associated with the exploited vulnerabilities.
Data Validation and Input Testing
Evaluate how the application handles user inputs and validate data validation mechanisms. Testers aim to identify vulnerabilities such as SQL injection and Cross-Site Scripting by manipulating input fields. Ensuring robust validation mechanisms is crucial to prevent malicious code injection and data manipulation attacks.
-
Reporting And Recommendations
Finally, the report! During this stage, testers compile a comprehensive report detailing vulnerabilities found, their risks, and recommended fixes. Explain the vulnerabilities’ effects in simple terms and offer suggestions for strengthening security posture. This report will help custom web application developers create a safe system and anticipate any weaknesses.
Read the 7 stages of web application development processes.
Top 5 Web Application Penetration Testing Tools for Security Professionals
Web security professionals rely on various tools to conduct thorough assessments. These tools offer security experts the ability to spot faults, simulate attacks, and improve the general security posture of online applications. Here are the top 5 tools used in a web application penetration testing methodology.
Best Practices of Web Application Penetration Testing
As a leading web app development company, we have successfully delivered flawless applications in various domains. Here are a few of our tried-and-tested smart tips to effectively implement a web application penetration testing methodology.
- Clearly define the scope of the test to avoid unintended consequences.
- Obtain proper authorization before conducting any penetration testing.
- Properly document all findings, including vulnerabilities and remediation recommendations.
- Maintain open communication with stakeholders throughout the testing process.
- Prioritize identified vulnerabilities based on their impact and likelihood of exploitation.
- Must follow ethical guidelines, respecting privacy and confidentiality during testing.
- Verify the effectiveness of remediation efforts through post-testing assessments.
- Keep up with the most recent security trends and update procedures as necessary.
Final Call
We believe that after reading this blog, it is clear to you that a web application penetration testing methodology is crucial for ensuring the security and resilience of digital assets. By systematically simulating cyber-attacks, these methodologies identify vulnerabilities and weaknesses in custom web applications.
In an era of ever-evolving cyber threats, adherence to these methodologies helps meet regulatory requirements and fosters a continuous improvement mindset, enhancing an organization’s ability to safeguard sensitive data, maintain business continuity, and adapt to emerging security challenges.
Do you have any queries about these standards and procedures for web application penetration testing methodologies? Are you curious about the benefits web app penetration testing can offer your company? To determine how penetration tests might improve your overall cybersecurity, speak with our QA team.
Frequently Asked Questions
-
How long will it take to do a web application pentest?
The duration of a web application penetration test depends on factors like the application’s complexity, size, and the testing scope. Typically, it ranges from a few days to several weeks, ensuring a thorough assessment.
-
How much does web app penetration testing cost?
The cost of web application penetration testing varies based on factors such as the complexity of the application, testing scope, and the depth of assessment required. Small-scale tests may start around $3,000, while larger or more intricate projects can exceed $25,000.
At eLuminous Technologies we offer customized quotes to address specific needs.
-
How to choose the best tester for your web application?
Choose the best web application tester by considering their experience, certifications (e.g., Certified Ethical Hacker), industry knowledge, and the ability to understand your application’s technology stack. Request references, evaluate past work, and ensure ethical and transparent communication to select a right tester aligned with your security needs.
QA Lead
Having 16+ years of experience in Quality Assurance and software testing. He is ISTQB certified and certified in Security Testing (EHE & NDE). His skill set includes Agile-Scrum methodologies, Quality Assurance, Manual & Automation with Selenium, Mobile App Testing, and Performance Testing.