Top Cloud Security Risks: Safeguarding Your Enterprise Data from Threats
Remember the days when we used to store all our data on physical drives and disks? However, that’s not the case now. Be it personal information or business, the volume of data we have now is vast, making it impossible to manage, carry around, and store it in physical devices with limited storage.
Then what?
Enter cloud storage — your solution to limitless storage capacity and accessibility. But just like storing valuables in a safe has its own risks, cloud storage comes with its own set of cloud security risks. With cyber threats evolving, understanding these cloud security risks has become crucial for protecting your organization’s data. If you do not pay attention to them, it can lead to repercussions that no one wants to face.
In this blog, we will discuss major cloud security risks and how to manage them effectively so that you stay updated and safe. Let’s get started without wasting much time!

What are Cloud Security Risks?
Cloud security risks are potential threats that could compromise the confidentiality, integrity, or availability of your data stored in cloud environments. These risks arise because cloud platforms operate on shared infrastructure, handle large volumes of data, and are accessible over the internet.
Unlike traditional IT systems, cloud environments introduce additional layers of complexity, from multi-tenant architectures to third-party service dependencies, making them more prone to vulnerabilities if not managed carefully.
Some common factors that contribute to cloud security risks include:
- Mistakes in setting up access controls, storage permissions, or encryption can expose sensitive data.
- Relying on weak passwords or a lack of multi-factor authentication increases the risk of unauthorized access.
- Cloud providers secure the infrastructure, but users are often responsible for their data, identity, and access management.
- Mistakes by employees or malicious insiders can lead to security breaches.
- Hackers constantly look for ways to exploit cloud platforms through malware, ransomware, or phishing attacks.
Understanding these risks is the first step toward building a secure cloud environment that protects both your data and business operations.
Cloud Security Risks

Businesses like yours are increasingly adopting cloud services. Therefore, knowing and understanding the associated cloud security risks is essential to protecting your business. Here’s an in-depth look at the major cloud security risks, why they occur, and effective strategies to overcome them.
| Sr. No | Cloud Security Risks | Solutions |
| 1. | Data Breaches |
|
| 2. | Data Loss |
|
| 3. | Account Hijacking |
|
| 4. | Insecure APIs |
|
| 5. | DDoS Attacks |
|
| 6. | IAM Weaknesses |
|
| 7. | Insider Threats |
|
| 8. | Compliance Risks |
|
1. Data Breaches
Data breaches, one of the popular cloud security risks, occur when an unauthorized individual gains access or tries to access sensitive data stored in the cloud. These breaches can happen if your cloud services have weak security measures, poor access controls, or vulnerabilities. This could lead your business to significant financial losses, reputational damage, and legal consequences. According to IBM’s Cost of Data Breach Report, the average cost of a data breach was $4.45 million in 2023.

How to Overcome them?
To overcome data breaches, implement strong encryption for data both at rest and in transit. This ensures that even if your data is intercepted, it remains unreadable without decryption keys. You can adopt zero-trust architecture, which assumes no entity inside or outside the network can be trusted, minimizing access vulnerabilities. Keep updating your encryption protocols regularly and use advanced encryption standards (AES) to provide additional security to your cloud data.
2. Data Loss
Data loss results from accidental deletion, data corruption, hardware failures, or natural disasters that lead to the inaccessibility of critical business information. This cloud security risk can disrupt business operations and result in the loss of valuable data. Gartner issued a report stating that through 2025, 99% of cloud security failures will be the customers’ fault, often due to data management issues.

How to Overcome them?
Back up your data regularly and ask your IT team to develop a comprehensive disaster recovery plan to ensure quick restoration of the lost data. These automated backup solutions will consistently back up the data without manual intervention. They will also ensure the reliability of backup processes, implement redundancy, where data is stored in multiple locations, and conduct regular backup integrity checks. This will prevent your business from this cloud security risk.

Do you want your business to achieve scalability in cloud computing? If yes, then Cloud Scalability Guide is here to learn more about it!
3. Account Hijacking
Account hijacking is when attackers gain unauthorized access to cloud accounts. This can lead to potential data theft of your business and unauthorized transactions. This risk often occurs due to weak passwords, phishing attacks, or poor authentication practices.

How to Overcome them?
To prevent account hijacking of your business, use multi-factor authentication (MFA). It significantly enhances your security by requiring multiple forms of verification before granting access to your account. Also, monitor your account activity continuously, as it will help you promptly detect and respond to suspicious behavior. Implement strong password policies and regular password changes to prevent unauthorized access.
4. Insecure APIs
APIs are essential for cloud service interactions but can be vulnerable if you don’t secure them properly. Insecure APIs can occur if you follow poor coding practices, lack authentication, or use outdated API protocols. Exploited API vulnerabilities can lead to data breaches and unauthorized access to your accounts. In a report, Gartner claimed API abuses will be the most frequent vector attack on enterprise web applications.
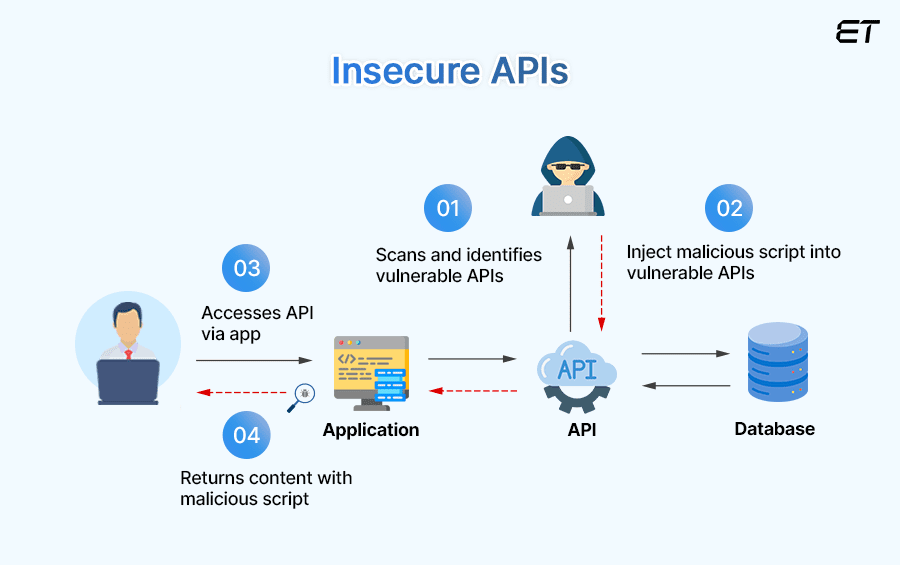
How to Overcome them?
You should conduct regular security testing of APIs, including penetration testing and code reviews, to identify and address vulnerabilities (if any). Implementing API gateways can manage and secure your API traffic, ensuring only legitimate requests are processed. You can also further reduce the risk of exploitation by adopting secure coding practices and keeping API documentation up to date.
5. Distributed Denial of Service (DDoS) Attacks
DDoS attacks flood cloud services with excessive traffic, causing your services to be unavailable to the users. These attacks can lead your business to a significant revenue loss and damage your reputation. They typically occur because of insufficient network security measures and inadequate infrastructure scalability.
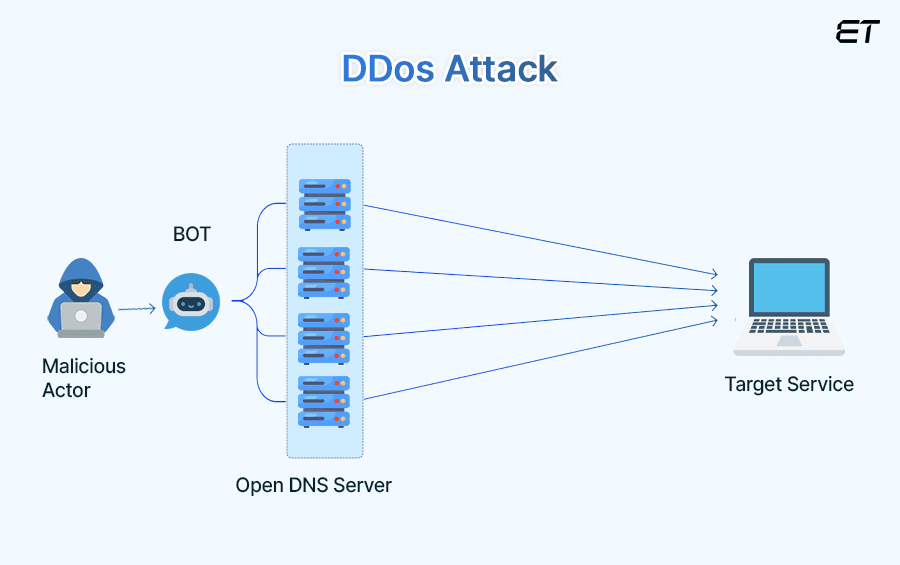
How to Overcome them?
Use DDoS protection services to help you detect and mitigate attacks before they impact your service availability. Ensure scalable infrastructure that can handle traffic spikes and implement rate limitations to reduce the effectiveness of DDoS attacks. You should also implement a DDoS response plan to ensure a quick reaction to mitigate the impact.
6. Insufficient Identity and Access Management (IAM)
Insufficient Identity and Access Management (IAM) is a framework of policies that verifies relevant access to resources for users to avoid any cloud security risk. Weak IAM practices can lead to unauthorized access to sensitive resources. Poor access controls, such as excessive permissions and lack of regular audits, can increase the risk of data breaches and insider threats to your firm.
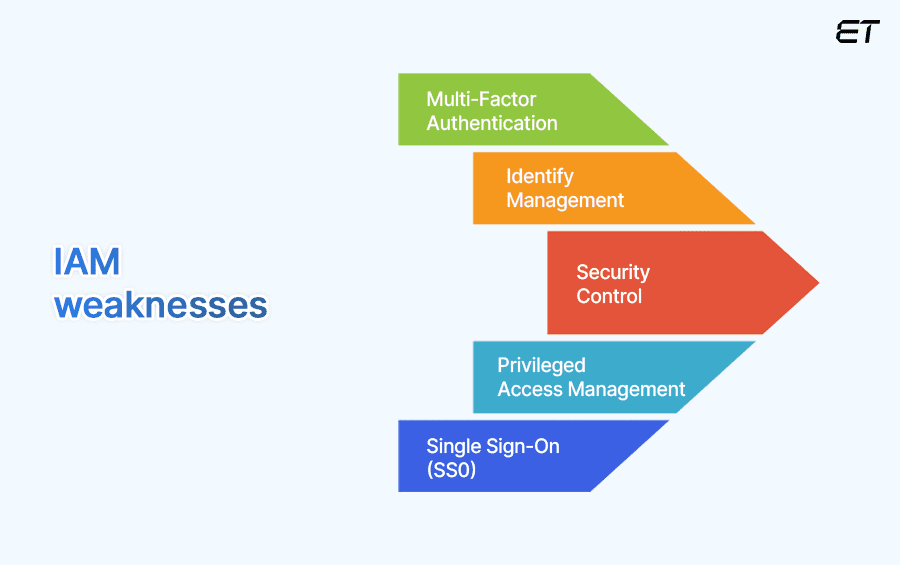
How to Overcome them?
To overcome this cloud security risk, you must ensure strong IAM practices like role-based access control (RBAC) and privileged access management (PAM). This ensures that only authorized users can access particular or critical resources. You can further enhance your security by regularly reviewing and updating access permissions and using identity federation. To add an additional layer of protection, you can employ zero-trust principles, where each access request is verified.

Facing issues in migrating to the cloud? Don’t worry! Your solution is just a click away. Discover best cloud migration tools in 2024 here.
7. Insider Threats
Insider threats imply risks posed by your employees or an internal member who may mishandle data or intentionally want to cause harm to your enterprise. These threats result from negligence, malicious intent, or lack of security awareness.

How to Overcome them?
To prevent your business from insider threats, monitor the behavioral aspects of the employees. This will help you in detecting usual activities that may indicate insider threats. Protect your data from being misused by enforcing strict access controls and using data loss prevention (DLP) tools. You can even organize regular security training and awareness programs to educate your employees about cloud security risks, best practices and the importance of data security.
8. Compliance and Legal Risks
Non-compliance with data protection regulations can lead your business to legal penalties and fines exposing it to major cloud security risks. It might also cause a loss of business trust among your audience. Regulations like GDPR and CCPA impose strict requirements on data handling and privacy. These risks occur due to inadequate compliance programs and a lack of awareness of regulatory changes.
Best Practices for Mitigating Cloud Security Risks
Managing cloud security isn’t just about responding to threats, but about building a strong defense before risks become problems. By following the proper practices, you can protect your data, applications, and your users in the cloud.
Here are some proven best practices for reducing cloud security risks:
- Implement strong access controls: Use role-based access controls and the principle of least privilege. Grant users only the permissions they need to perform their tasks.
- Enforce multi-factor authentication (MFA): MFA adds an extra layer of security by requiring you to verify your identity, more than just once.
- Regularly monitor and audit cloud activities: Track user actions, configuration changes, and data access through continuous monitoring tools. This helps you detect suspicious activities early.
- Encrypt data at rest and in transit: Always encrypt sensitive data, whether it’s stored on cloud servers or moving between systems. Encryption makes it harder for attackers to misuse stolen data.
- Keep cloud configurations in check: Use cloud security posture management (CSPM) tools to identify and fix misconfigurations that could leave your environment exposed.
- Backup data and test recovery plans: Regular backups and disaster recovery testing ensure your business continuity in case of data loss or ransomware attacks.
- Educate and train your team: Conduct regular security awareness training for your employees to reduce risks linked to human error or phishing attempts.
- Understand your cloud provider’s responsibility: Know which security aspects are managed by your provider and which are your responsibility. This clarity helps avoid security gaps.
How to Overcome them?
To keep your cloud computing experience secure, conduct regular compliance audits. This way, you can ensure that your cloud infrastructure meets the current regulatory standards. Keep policies and procedures updated to reflect the latest compliance requirements. You can also use compliance management tools to simplify your audit process. Further, you can also benefit from engaging with legal experts to understand regulatory requirements and avoid any type of cloud security risks.
Real-World Examples of Cloud Security Risks
Now that we have come so far learning about cloud security risks, let’s understand practically what companies have faced:
1. Capital One’s AWS Misconfiguration
In 2019, a firewall misconfiguration on Amazon Web Services allowed attacker Paige Thompson to exploit a server-side request forgery (SSRF) vulnerability. It exposed personal data of approximately 100 million U.S. customers and 6 million Canadians, including names, addresses, 140,000 Social Security numbers, and 80,000 bank account numbers. The incident cost Capital One an estimated US$100–150 million in immediate response efforts.
2. Accenture’s Open S3 Buckets
In September 2017, Accenture left four AWS S3 buckets publicly accessible, which contained over 137 GB of data, including 40,000 plaintext passwords, private keys, and credentials across multiple platforms. The exposure risked client data and deepened concerns over human error in cloud configurations.
3. Microsoft Power Apps Leak
Misconfigured Power Apps portals inadvertently exposed approximately 38 million records from over 1,000 web applications. The leaks included sensitive information such as social security numbers, health data, contact-tracing records, and vaccination details across public agencies and corporations, including American Airlines and Ford.
Wrapping Up!
Tackling the complexities of cloud security is no small feat, but it’s absolutely essential for safeguarding your enterprise’s data and smooth business operations. As cloud adoption continues to rise, so do the associated risks, making it imperative to stay ahead of the potential threats.
From data breaches and loss to account hijacking to insecure APIs, the risks are multifaceted, and so should your strategy be. Taking precautions and advanced measures will enhance your business’s security and build resilience against future threats.
As it is rightly said– “Prevention is better than cure.” And we at eLuminous Technologies understand that very well. We are committed to helping your business mitigate your cloud security risks and strengthen your cloud security posture management. Our tailored solutions ensure that your cloud infrastructure remains robust and secure so that you can focus on your core business objectives. So what are you waiting for? Contact us today and let us guide you through the complexities of cloud security risk management.
Frequently Asked Questions
1. What is risk in cloud security?
Cloud security risks refer to the possibility of unauthorized access, data breaches, or service disruptions within the cloud. These risks occur due to several factors like misconfigurations, weak access controls, or shared infrastructure vulnerabilities.
2. What is the biggest threat to security on cloud?
The biggest threat to cloud security is misconfiguration. Whether it’s open storage buckets, weak access permissions, or incorrect firewall settings, misconfigurations are often the easiest way for attackers to exploit your cloud systems.
3. What are the main challenges in cloud security?
Some of the main cloud security risks and challenges you can face today include:
- Data breaches and leaks: Sensitive information can be exposed due to poor access controls or insecure storage.
- Misconfigurations: Incorrect cloud settings can leave your systems open to attacks.
- Identity and access management (IAM) issues: Poor user access policies can lead to unauthorized access to sensitive data.
- Compliance and regulatory requirements: Meeting industry-specific security regulations across multiple regions can be a complex task.
Visibility and control: Monitoring data flow and user activities in cloud is often harder than in on-premises systems.
Third-party and supply chain risks: Cloud providers, vendors, or partners may introduce security gaps that compromise the integrity of your system.